For devices running Android 13 or higher, Android supports the Trust on First Use (TOFU) authentication approach (RFC7435), which lets users trust an enterprise (EAP) network by installing the root CA used by the server and setting its domain name in a saved network. TOFU allows the device to obtain an unauthenticated public key when a user first connects to an enterprise network and retain the key for subsequent connections.
Background
Compared to personal networks that just require a password, enterprise networks use public key infrastructure (PKI) authentication, which requires the client to preinstall certificates. In Android 11 or lower, users can select the Do not validate option for the server CA certificate in the network settings, bypassing the validation of the server side certificate. However, to strengthen security and comply with the WPA R2 specification, Android 12 introduced a requirement for enterprise networks to have server certificate validation. This additional requirement created a barrier for users as they need to install a CA certificate for such networks. TOFU provides a way for users to connect to a PKI-based enterprise network by accepting its root CA.
Feature behavior
Devices that support TOFU display the following behavior when a user connects to an enterprise network that doesn't have an already-installed authenticated public key.
Connect to new network through Wi-Fi picker
Select a new enterprise network in Wi-Fi picker.
The device displays a dialog (Figure 1) to confirm whether the network is trusted.
Tap Yes, connect to accept the network connection, or tap No, don't connect to decline.
If you tap Yes, connect, the device automatically configures the security parameters, connects to the network, and enables auto-connect for the network.
If you tap No, don't connect, the device disconnects from the network and disables auto-connect for the network.
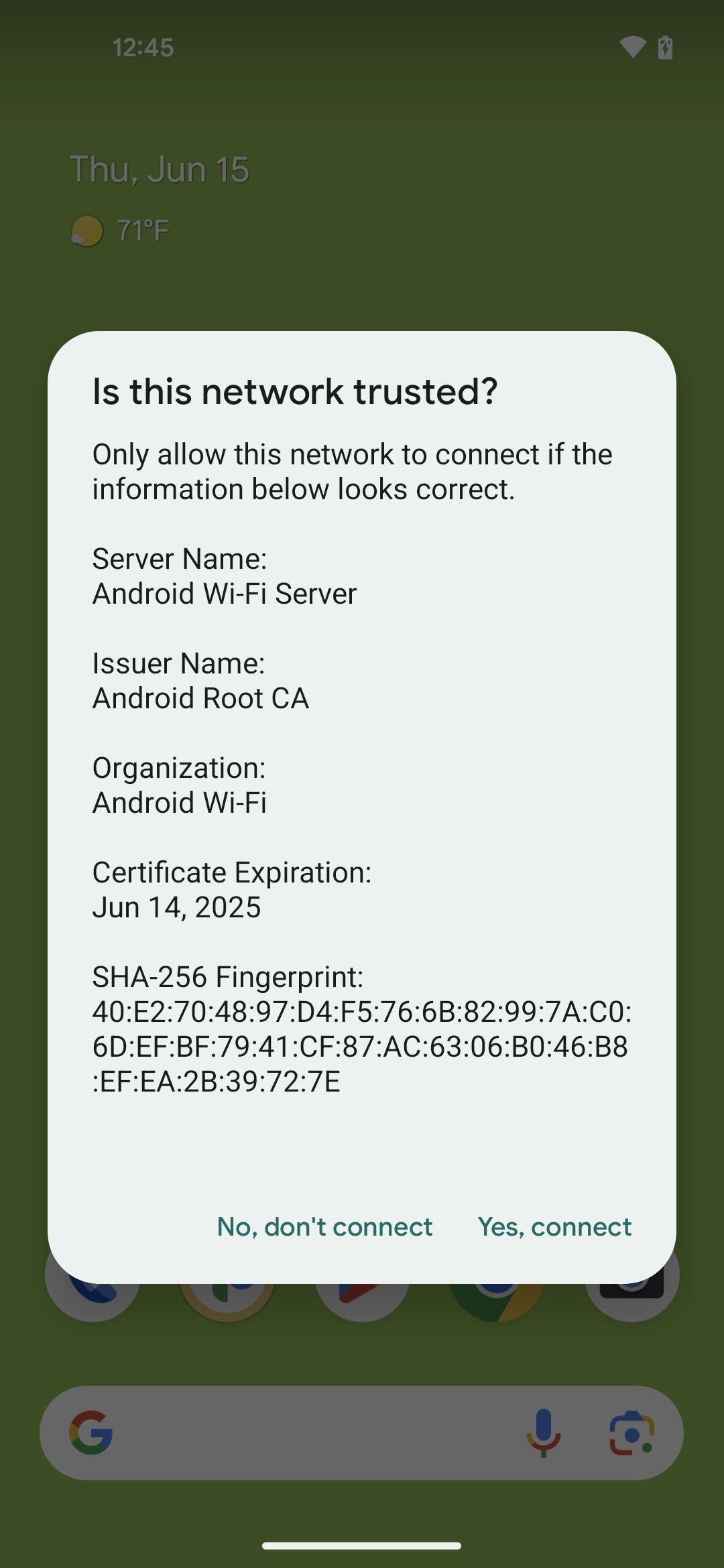
Figure 1. Dialog for the TOFU feature
Connect to existing network with auto-connect enabled
When connecting to an enterprise network that has auto-connect enabled but doesn't have a valid CA certificate, the device connects automatically, then displays a sticky (nondismissable) notification.
Tap the notification.
The device displays a dialog (Figure 1) to confirm whether the network is trusted.
Tap Yes, connect to accept the network connection, or tap No, don't connect to decline.
If you tap Yes, connect, the device automatically configures the security parameters, connects to the network, and enables auto-connect for the network.
If you tap No, don't connect, the device disconnects from the network and disables auto-connect for the network.
Implementation
To support the TOFU feature, implement the supplicant HALs provided in the
Android Open Source Project (AOSP) at
/hardware/interfaces/wifi/supplicant/aidl/android/hardware/wifi/supplicant.
The following public APIs are available in Android 13 for use by apps:
WifiManager#isTrustOnFirstUseSupported(): Indicates whether the device supports TOFU.WifiEnterpriseConfig#enableTrustOnFirstUse(boolean): Enables TOFU.WifiEnterpriseConfig#isTrustOnFirstUseEnabled(): Indicates whether TOFU is enabled.
Validation
To validate the implementation of TOFU on your device, use the following tests:
- CTS:
CtsWifiTestCases - VTS:
VtsHalWifiSupplicantStaNetworkTargetTest
